Understanding Keychain
Securing Sensitive Data in iOS - The Importance of Keychain and iCloud Keychain
In the modern digital age, where data breaches and cyber threats are increasingly common, securing sensitive user data is a critical responsibility for developers. Whether it’s passwords, cryptographic keys, or personal information, ensuring that this data is stored securely on a device is paramount. For iOS developers, the Keychain and iCloud Keychain provide robust solutions for secure data storage. This article explores the importance of these tools, how they work, and best practices for implementation.
What is Keychain?
The Keychain is a secure storage container provided by Apple for iOS and macOS platforms. It allows developers to store sensitive information such as passwords, cryptographic keys, certificates, and other data that needs to be protected from unauthorized access. Unlike other forms of local storage, such as UserDefaults or file storage, the Keychain is designed with security in mind, offering encryption and access control mechanisms that ensure the confidentiality and integrity of the data.
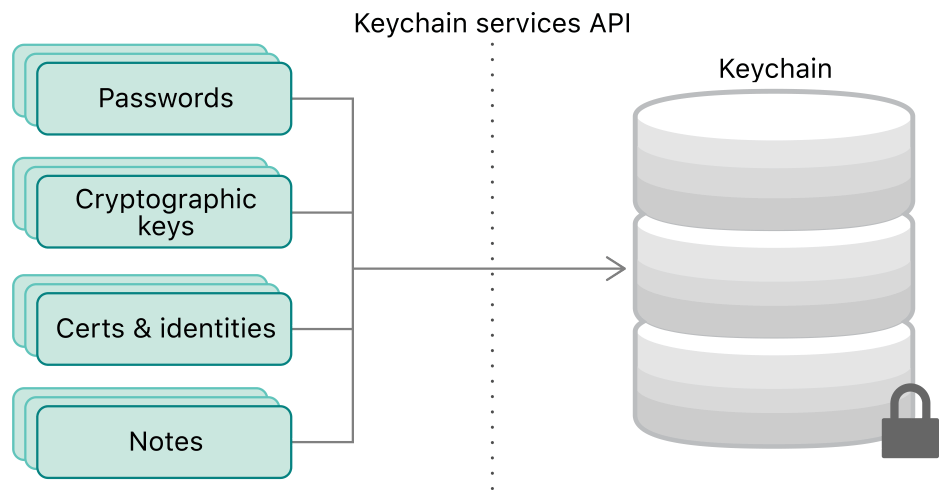
Why Use Keychain?
-
Security: The primary reason to use Keychain is its strong security features. Data stored in the Keychain is encrypted using the device’s unique hardware security, making it nearly impossible for attackers to retrieve the information, even if they have physical access to the device. Additionally, the Keychain is protected by the user’s device passcode, Face ID, or Touch ID, adding an extra layer of security.
-
Persistence: Keychain data persists across app installations and updates. This means that even if a user deletes and reinstalls your app, their sensitive data, such as login credentials, remains intact. This persistence is particularly useful for improving user experience, as it eliminates the need for users to re-enter their credentials after reinstalling an app.
-
Access Control: The Keychain allows developers to specify the level of access control for each piece of data. For instance, you can set items to be accessible only when the device is unlocked, or even require additional authentication (like Face ID) before accessing the data. This flexibility ensures that sensitive information is only accessible under appropriate conditions.
-
Multi-App Access: The Keychain supports sharing data between multiple apps from the same development team using a Keychain Access Group. This feature is particularly useful for apps that need to share authentication tokens or other secure information.
-
Compliance: For developers working in industries with strict regulatory requirements (e.g., finance, healthcare), using Keychain helps in meeting compliance standards such as GDPR or HIPAA. The built-in encryption and access controls can aid in demonstrating that user data is being handled securely.
Common Use Cases for Keychain
-
Storing User Credentials: The most common use case for Keychain is storing user credentials, such as usernames and passwords. By keeping these credentials secure, you can ensure that users’ accounts are protected from unauthorized access.
-
Secure API Tokens: Many apps interact with backend services using API tokens. Storing these tokens in Keychain prevents them from being exposed to unauthorized parties, thereby safeguarding communication between your app and the server.
-
Cryptographic Keys: If your app involves encryption or signing operations, Keychain is the ideal place to store cryptographic keys. Storing keys securely is crucial, as the compromise of these keys can lead to severe security breaches.
-
Storing Sensitive App Data: Beyond credentials and keys, Keychain can be used to store other sensitive data, such as payment information, health data, or private user preferences that should remain confidential.
| Feature | Keychain | UserDefaults | File Storage |
|---|---|---|---|
| Purpose | Store sensitive data securely | Store simple user preferences | Store files and large datasets |
| Security Level | High (encrypted by OS) | Low (not encrypted) | Medium (depending on storage method) |
| Data Type | Small, sensitive items (e.g., tokens, passwords) | Basic data types (e.g., strings, booleans, arrays) | Any file format (e.g., text, images, JSON) |
| Encryption | Yes | No | Optional (depends on implementation) |
| Persistence | Long-term | Long-term (until app uninstall) | Long-term (dependent on app logic) |
| Typical Usage | Storing credentials, secrets, API keys | Storing user settings, preferences | Storing documents, images, large data sets |
| Accessibility | Controlled by iOS security policies | Accessible directly in app | Can be accessed via file system APIs |
| Sync Capability | Can be synced using iCloud Keychain | Can be synced via iCloud | Can be backed up manually or using iCloud |
| Storage Limit | Limited, not suitable for large data | Limited to small amounts of data | No fixed limit, constrained by device storage |
| Ease of Use | Moderate complexity | Very easy to use | Moderate to complex, depending on file handling |
| Examples | Storing user authentication tokens | Saving a “dark mode” setting | Saving user-generated content (photos, documents) |
Linking Keychain to iCloud storage
Linking Keychain to iCloud storage, known as iCloud Keychain, offers several significant benefits, particularly in terms of data security, accessibility, and convenience. Here’s are some of the detailed look at the advantages:
1. Data Synchronization Across Devices
- Automatic Syncing: iCloud Keychain automatically syncs your Keychain items across all Apple devices signed in with the same Apple ID. This includes passwords, credit card information, Wi-Fi network credentials, and more.
- Seamless Experience: When you save a password on one device, it is instantly available on all other devices, allowing for a seamless experience when switching between an iPhone, iPad, Mac, or even an Apple Watch.
- No Manual Transfers: Users don’t need to manually transfer or re-enter their information when they get a new device or use multiple devices. Everything is already available as soon as they sign in with their Apple ID.
2. Enhanced Security
- End-to-End Encryption: iCloud Keychain uses end-to-end encryption, meaning that only the user can access their Keychain data. Even Apple cannot access this information because the encryption keys are stored on the user’s devices.
- Protection Against Loss: If a device is lost or damaged, iCloud Keychain ensures that your passwords and other sensitive data are not lost. They can be easily restored on a new device by signing in with your Apple ID.
3. Easy Setup and Recovery
- Simple Setup: Once iCloud Keychain is enabled, there’s minimal setup required. All credentials are synced without needing extra steps from the user.
- Account Recovery: If a user forgets their device passcode or Apple ID password, they can recover their iCloud Keychain data using account recovery options. This provides an additional safety net for accessing important information.
4. Secure Sharing and Auto-Fill
- Password Sharing: iCloud Keychain allows for secure sharing of passwords with trusted contacts or across family members using Apple’s family sharing feature.
- Auto-Fill: With iCloud Keychain, passwords and payment information can be auto-filled across all your Apple devices, making logging in and completing transactions faster and more convenient while maintaining high security.
5. Minimal User Effort
- No Need for Third-Party Apps: Users don’t need to rely on third-party password managers when using iCloud Keychain, as it provides comprehensive password management features natively integrated into iOS, iPadOS, and macOS.
- Less Cognitive Load: Since iCloud Keychain remembers all credentials and securely stores them, users don’t need to memorize complex passwords or go through the hassle of resetting passwords frequently.
6. Integrated with Safari and Apps
- Browser Integration: iCloud Keychain is deeply integrated with Safari, Apple’s default browser, making it easy to save and retrieve passwords, credit card details, and forms data directly in the browser.
- App Integration: Many apps on iOS and macOS can directly access Keychain data for authentication, further streamlining the login process without compromising security.
7. Automatic Password Generation and Alerts
- Strong Password Suggestions: iCloud Keychain suggests strong, unique passwords when creating new accounts, which are then automatically stored and synced across devices.
- Security Alerts: iCloud Keychain can alert users if a password has been reused across multiple sites or if it has been involved in a data breach, prompting the user to change the password.
Best Practices for Using Keychain
-
Minimal Data Storage: Store only the most sensitive data in the Keychain. For less sensitive data, consider using other storage mechanisms with appropriate security measures.
-
Use Access Control Wisely: Take advantage of Keychain’s access control options to limit when and how data can be accessed. For example, use
kSecAttrAccessibleWhenUnlockedto ensure that data is only accessible when the device is unlocked. Check out “Overview ofkSecClassConstants” section for more. -
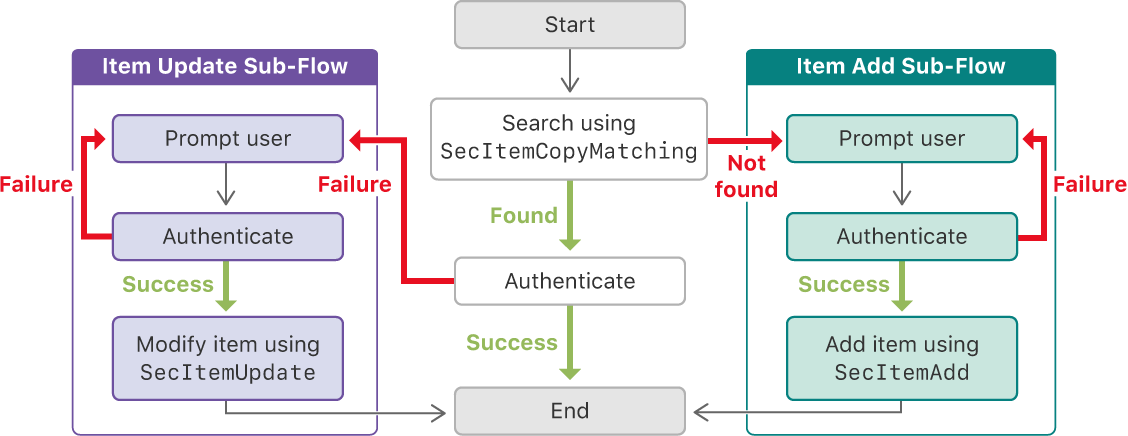
Handle Errors Gracefully: Always check the status code returned by Keychain operations (e.g.,
SecItemAdd,SecItemCopyMatching) and handle errors appropriately. This ensures that your app can respond to issues like insufficient permissions or missing data. -
Test Keychain Behavior Across App Installations: Test your app’s behavior across different scenarios, such as app reinstallation or OS updates, to ensure that Keychain data persists as expected.
-
Avoid Storing Large Amounts of Data: The Keychain is not intended for storing large amounts of data. Instead, use it for small pieces of sensitive information, such as passwords or tokens.
Overview of `kSecClass` Constants
 When working with the Keychain, you use a dictionary of key-value pairs to specify what data you want to store, retrieve, update, or delete. One of the most important keys in this dictionary is `kSecClass`, which defines the type of item you are dealing with (e.g., a password, a key, a certificate).
*Keychain Item Classes (`kSecClass` Constants)*
The `kSecClass` constants are used to specify the type of item you want to work with in the Keychain. Below are the most commonly used constants:
- **`kSecClassInternetPassword`**: Used for storing internet-based passwords, such as those for websites or online services.
- **`kSecClassGenericPassword`**: Used for storing any kind of generic password that doesn't fall under a specific category, such as API tokens or application-specific passwords.
- **`kSecClassCertificate`**: Used for storing certificates, typically X.509 certificates used in SSL/TLS connections.
- **`kSecClassKey`**: Used for storing cryptographic keys, including symmetric keys, private keys, and public keys.
- **`kSecClassIdentity`**: Used for storing identities, which are a combination of a private key and its associated certificate.
### Detailed Examples
#### 1. Storing an Internet Password (`kSecClassInternetPassword`)
Suppose you want to store a password for a website in the Keychain. Here's how you can do it:
swift
```
import Security
let account = "user@example.com"
let password = "mySecurePassword"
let service = "example.com"
let passwordData = password.data(using: .utf8)!
let query: [String: Any] = [
kSecClass as String: kSecClassInternetPassword,
kSecAttrAccount as String: account,
kSecAttrServer as String: service,
kSecValueData as String: passwordData
]
let status = SecItemAdd(query as CFDictionary, nil)
if status == errSecSuccess {
print("Password successfully added to Keychain.")
} else if status == errSecDuplicateItem {
print("Password already exists in Keychain.")
} else {
print("Error adding password to Keychain: \(status)")
}
```
- **Explanation**:
- **`kSecClass`:** Specifies that we are storing an Internet password.
- **`kSecAttrAccount`:** The username or account associated with this password.
- **`kSecAttrServer`:** The server (domain) where the password will be used.
- **`kSecValueData`:** The actual password data to be stored.
#### 2. Retrieving a Generic Password (`kSecClassGenericPassword`)
Now, let's say you want to retrieve a password stored under a specific account in your app:
```
import Security
let account = "user@example.com"
let service = "myApp"
let query: [String: Any] = [
kSecClass as String: kSecClassGenericPassword,
kSecAttrAccount as String: account,
kSecAttrService as String: service,
kSecReturnData as String: kCFBooleanTrue!,
kSecMatchLimit as String: kSecMatchLimitOne
]
var item: CFTypeRef?
let status = SecItemCopyMatching(query as CFDictionary, &item)
if status == errSecSuccess, let passwordData = item as? Data, let password = String(data: passwordData, encoding: .utf8) {
print("Password retrieved: \(password)")
} else {
print("Failed to retrieve password: \(status)")
}
```
- **Explanation**:
- **`kSecClass`:** Specifies that we are looking for a generic password.
- **`kSecAttrAccount`:** The account associated with the password.
- **`kSecAttrService`:** The service (or app) that the password is associated with.
- **`kSecReturnData`:** Specifies that we want the password data to be returned.
- **`kSecMatchLimit`:** Limits the search to one matching item.
#### 3. Updating a Keychain Item
To update an existing password:
```
import Security
let account = "user@example.com"
let service = "myApp"
let newPassword = "newSecurePassword"
let newPasswordData = newPassword.data(using: .utf8)!
let query: [String: Any] = [
kSecClass as String: kSecClassGenericPassword,
kSecAttrAccount as String: account,
kSecAttrService as String: service
]
let attributesToUpdate: [String: Any] = [
kSecValueData as String: newPasswordData
]
let status = SecItemUpdate(query as CFDictionary, attributesToUpdate as CFDictionary)
if status == errSecSuccess {
print("Password updated successfully.")
} else {
print("Failed to update password: \(status)")
}
```
- **Explanation**:
- **`SecItemUpdate`:** Updates the Keychain item specified by the query with the new attributes provided.
- **`attributesToUpdate`:** Specifies the new password data to replace the existing one.
#### 4. Deleting a Keychain Item
To delete an item from the Keychain:
```
import Security
let account = "user@example.com"
let service = "myApp"
let query: [String: Any] = [
kSecClass as String: kSecClassGenericPassword,
kSecAttrAccount as String: account,
kSecAttrService as String: service
]
let status = SecItemDelete(query as CFDictionary)
if status == errSecSuccess {
print("Password deleted successfully.")
} else {
print("Failed to delete password: \(status)")
}
```
- **Explanation**:
- **`SecItemDelete`:** Removes the Keychain item specified by the query.
The `kSecClass` constants are crucial because they allow the Keychain services to understand the type of item you are working with. This ensures that the correct storage, retrieval, and security policies are applied to the data. Without specifying `kSecClass`, the Keychain wouldn't know how to handle the data, leading to errors or unexpected behavior.
When working with the Keychain, you use a dictionary of key-value pairs to specify what data you want to store, retrieve, update, or delete. One of the most important keys in this dictionary is `kSecClass`, which defines the type of item you are dealing with (e.g., a password, a key, a certificate).
*Keychain Item Classes (`kSecClass` Constants)*
The `kSecClass` constants are used to specify the type of item you want to work with in the Keychain. Below are the most commonly used constants:
- **`kSecClassInternetPassword`**: Used for storing internet-based passwords, such as those for websites or online services.
- **`kSecClassGenericPassword`**: Used for storing any kind of generic password that doesn't fall under a specific category, such as API tokens or application-specific passwords.
- **`kSecClassCertificate`**: Used for storing certificates, typically X.509 certificates used in SSL/TLS connections.
- **`kSecClassKey`**: Used for storing cryptographic keys, including symmetric keys, private keys, and public keys.
- **`kSecClassIdentity`**: Used for storing identities, which are a combination of a private key and its associated certificate.
### Detailed Examples
#### 1. Storing an Internet Password (`kSecClassInternetPassword`)
Suppose you want to store a password for a website in the Keychain. Here's how you can do it:
swift
```
import Security
let account = "user@example.com"
let password = "mySecurePassword"
let service = "example.com"
let passwordData = password.data(using: .utf8)!
let query: [String: Any] = [
kSecClass as String: kSecClassInternetPassword,
kSecAttrAccount as String: account,
kSecAttrServer as String: service,
kSecValueData as String: passwordData
]
let status = SecItemAdd(query as CFDictionary, nil)
if status == errSecSuccess {
print("Password successfully added to Keychain.")
} else if status == errSecDuplicateItem {
print("Password already exists in Keychain.")
} else {
print("Error adding password to Keychain: \(status)")
}
```
- **Explanation**:
- **`kSecClass`:** Specifies that we are storing an Internet password.
- **`kSecAttrAccount`:** The username or account associated with this password.
- **`kSecAttrServer`:** The server (domain) where the password will be used.
- **`kSecValueData`:** The actual password data to be stored.
#### 2. Retrieving a Generic Password (`kSecClassGenericPassword`)
Now, let's say you want to retrieve a password stored under a specific account in your app:
```
import Security
let account = "user@example.com"
let service = "myApp"
let query: [String: Any] = [
kSecClass as String: kSecClassGenericPassword,
kSecAttrAccount as String: account,
kSecAttrService as String: service,
kSecReturnData as String: kCFBooleanTrue!,
kSecMatchLimit as String: kSecMatchLimitOne
]
var item: CFTypeRef?
let status = SecItemCopyMatching(query as CFDictionary, &item)
if status == errSecSuccess, let passwordData = item as? Data, let password = String(data: passwordData, encoding: .utf8) {
print("Password retrieved: \(password)")
} else {
print("Failed to retrieve password: \(status)")
}
```
- **Explanation**:
- **`kSecClass`:** Specifies that we are looking for a generic password.
- **`kSecAttrAccount`:** The account associated with the password.
- **`kSecAttrService`:** The service (or app) that the password is associated with.
- **`kSecReturnData`:** Specifies that we want the password data to be returned.
- **`kSecMatchLimit`:** Limits the search to one matching item.
#### 3. Updating a Keychain Item
To update an existing password:
```
import Security
let account = "user@example.com"
let service = "myApp"
let newPassword = "newSecurePassword"
let newPasswordData = newPassword.data(using: .utf8)!
let query: [String: Any] = [
kSecClass as String: kSecClassGenericPassword,
kSecAttrAccount as String: account,
kSecAttrService as String: service
]
let attributesToUpdate: [String: Any] = [
kSecValueData as String: newPasswordData
]
let status = SecItemUpdate(query as CFDictionary, attributesToUpdate as CFDictionary)
if status == errSecSuccess {
print("Password updated successfully.")
} else {
print("Failed to update password: \(status)")
}
```
- **Explanation**:
- **`SecItemUpdate`:** Updates the Keychain item specified by the query with the new attributes provided.
- **`attributesToUpdate`:** Specifies the new password data to replace the existing one.
#### 4. Deleting a Keychain Item
To delete an item from the Keychain:
```
import Security
let account = "user@example.com"
let service = "myApp"
let query: [String: Any] = [
kSecClass as String: kSecClassGenericPassword,
kSecAttrAccount as String: account,
kSecAttrService as String: service
]
let status = SecItemDelete(query as CFDictionary)
if status == errSecSuccess {
print("Password deleted successfully.")
} else {
print("Failed to delete password: \(status)")
}
```
- **Explanation**:
- **`SecItemDelete`:** Removes the Keychain item specified by the query.
The `kSecClass` constants are crucial because they allow the Keychain services to understand the type of item you are working with. This ensures that the correct storage, retrieval, and security policies are applied to the data. Without specifying `kSecClass`, the Keychain wouldn't know how to handle the data, leading to errors or unexpected behavior.
Where is Keychain Data Stored on iOS Devices?
The data stored in the Keychain on iOS devices is managed by the operating system and is not directly accessible by developers in terms of the physical memory location. However, here’s how the Keychain works under the hood:
-
Encrypted Storage: Keychain data is stored in an encrypted database managed by the iOS operating system. This database is secured by the device’s hardware security features, such as the Secure Enclave (on devices that have it) and the device’s unique identifier.
-
Secure Enclave: On devices that include a Secure Enclave, this coprocessor handles encryption operations and secures the keys used for encrypting and decrypting Keychain items. The Secure Enclave is isolated from the main processor to provide an extra layer of security, ensuring that sensitive operations are protected even if the main OS is compromised.
-
Apple File System (APFS): In APFS, the exact location of the Keychain database on the filesystem is not publicly documented (and for security reasons, it is kept abstracted from developers), it is typically stored in a part of the filesystem that is encrypted and protected by the system. This ensures that even if someone gains physical access to the device’s storage, they cannot easily extract Keychain data without the necessary encryption keys.
What Happens if the Device is Out of Memory?
The Keychain is designed to store small pieces of data, such as passwords, cryptographic keys, and certificates. Given that this data is generally small in size, the likelihood of the Keychain consuming a significant amount of memory is low.
However, in general, when an iOS device is running low on memory:
-
System Memory Management: iOS manages memory dynamically and will start freeing up memory used by applications that are in the background. It will also clear caches and temporary files, and may kill background processes to free up RAM.
-
Persistent Storage: Since Keychain data is stored persistently (similar to files on disk), it is not held in memory (RAM) during normal operation. Instead, Keychain items are only loaded into memory temporarily when they are accessed by an application. After access, the data is usually cleared from memory to ensure security and to free up resources.
-
Low Storage: If the device’s storage is completely full (not just RAM but the entire disk space), iOS will start to restrict certain operations, but the Keychain itself is unlikely to be affected directly. In extreme cases of low storage, the system may prevent new data from being added to the Keychain until space is freed up. However, existing Keychain data will remain intact and secure.
References:
Here are some useful Apple documentation links and resources that can help you understand and work with Keychain, iCloud Keychain, and secure data storage on iOS:
Keychain Services Reference
- This reference document details the Keychain API, including functions, constants, and data types you’ll need when working with Keychain.
- Link: Keychain Services Reference
iCloud Keychain Overview
- This document gives an overview of iCloud Keychain, explaining how it works, what it stores, and how to manage it across devices.
- Link: iCloud Keychain Overview
Security Framework Reference
- This document provides an in-depth look at the Security framework in iOS, which includes Keychain services, encryption, certificates, and trust policies.
- Link: Security Framework Reference
Using the Keychain to Store Private Data
- A practical guide that explains how to securely store data in the Keychain using Swift. This guide includes examples and best practices.
- Link: Using the Keychain to Store Private Data
Apple’s iOS Security Guide
- A detailed document that explains the security technologies and features implemented in iOS, including those related to Keychain and data protection.
- Link: iOS Security Guide
8. Best Practices for Managing Secrets in Your iOS App
- This docuement provides an overview of how to manage secrets in iOS apps, including best practices for using the Keychain and secure storage.
- Link: Managing Secrets in iOS Apps
These resources should provide you with a solid foundation for understanding and effectively using Keychain and iCloud Keychain in your iOS development projects.
Thanks for reading. Hope you found it interesting just like I did! :)